The thought of “servers” and “hosting” are rarely things you consider on a daily basis. If you are not an IT or a software architect, then probably not at all.
For the mentioned professionals, however, these decisions are critical to the operations of a business however large or small.
There is a fine line between how (and where) your software systems are used. This line has become thinner because of evolving cloud technology and automation.
Sourcing and deploying the right IT architecture could therefore help your business stay afloat, or sink without.
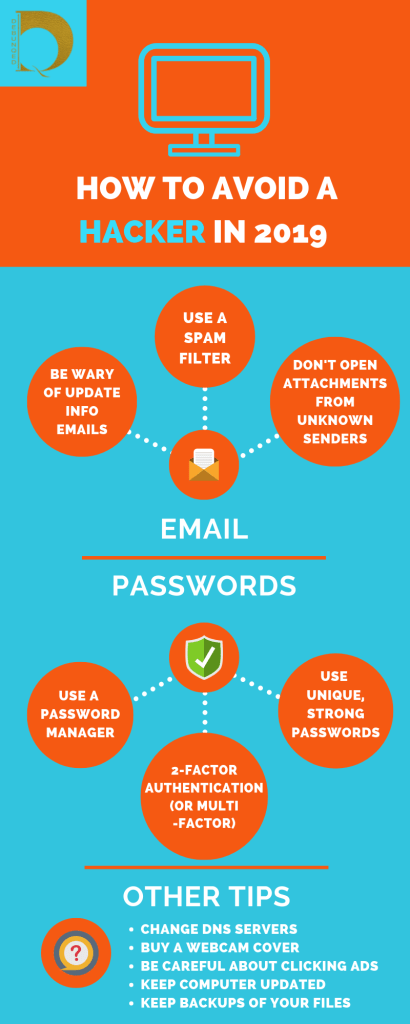
Communication is key
The most effective mode of communication in any business (other than verbally or telephonically) is still electronic mail (E-mail).
It is effective because it helps you get a time-stamp and a reference point when it comes to the documentation of your conversations. This is important tool when it comes to your legal obligations and commitments.
Emails are, therefore, something that should not be taken for granted!
We consequently send, receive emails with attachments through various devices. All this without a second thought as to how this happens.
After all, this is the job of the IT-guys, right?
Well quite rightly so. They often clash with their management and board of directors for funds to keep this going without compromising operations. Emails are crucial not only from a daily functional point of view but from security but also the compliance facet.
Defining servers
Your company’s IT infrastructure: Emails; File-servers; Databases (CRMs and ERPs) and other communication tools are commonly managed on-site on systems referred to as ‘on-premise’ solutions.
These are managed by computer-like CPUs that look like the standard boxes that you plug your monitor and keyboards. They, however, have a lot more processing power and storage than your average desktop and are called Servers.
Your servers naturally must be kept cool because of the heat they generate from being on all the time. As you can imagine, built-in fans are far from being enough to cool them off!
There an array of server types. Each of them is designed to run the tasks of your mail exchanges, file storage, and the storing/deploying of remote PC operating systems. Others handle your databases and other dedicated functions.
You would need to have the licensed software to operate each server providing unique services. This makes it quite an expensive outlay if you have all of the abovementioned requirements!
Servers are not irreplaceable and can overheat, get corrupted, or crash like a hard-drive (or a NAS server system). You, therefore, need to be maintain them at a cost to your business via your IT department.
Depending on the amount of data and complexity, the maintenance is outsourced to specialized IT companies or software license providers.
Cloud-computing
In the early 2000s, ‘the cloud’ or ‘cloud computing’ became a new concept. It is basically a very large set of high-end servers equipped with software to manage all the tasks mentioned above. It is usually offered as a service under a single (monthly or annual) subscription.
So basically, you are renting the service of a server as opposed to owning it. Renting, just like with property or cars, relieves the user of all the costs of maintaining the product in question.
This sort of rental service offered by cloud service providers is now known as Software as a Service (SaaS). This also saves you from purchasing any hardware let alone paying for the extra electricity bill to cool a server room.
According to Quora.com, the main difference between a cloud and a datacenter is that a cloud is an ‘off-premise’ form of computing that stores data on the Internet.
A Datacenter, on the other hand, is an on-premise set of hardware that stores data within an organization’s local network.
As an IT professional, you constantly face the burning question of whether to go for a solution that will relieve you of mundane tasks – like server maintenance. Naturally, you would also want a solution that facilitates the daily administering of user-profiles, data archiving, and backups. But to what costs then?
Deciding on which to go for
There are many pros and cons when it comes to the hosting of your company’s data on a local server as opposed to having it run via the cloud. There is also a massive array of choices and bundles between the top cloud service providers.
Cloud service providers have several data centers used as backups. So your email hosting may have several servers in different locations to serve that function. This curbs the risk of your data getting lost, unavailable, or hacked.
Naturally, Datacenters are kept highly secure in undisclosed locations globally. Google is known to have one of its datacenters floating on a massive container ship somewhere over the Atlantic ocean.
Maintenance
Maintaining a server is expensive as you require massive cooling systems. Some smarter companies like Microsoft, are now taking to the deep oceans for that function.
When it comes to email hosting or the storage of your files in the cloud only five large multinational corporations’ names come to mind. Microsoft, Oracle, Google, IBM, and Amazon.
These companies however bear the burden of maintenance, while providing just the service you require on a subscription basis.
Setting up an on-premise solution, in contrast, can be a tedious exercise and an expensive one. This is more applicable to smaller companies that do not have large IT budgets.
Licensing your server is no child’s play either!
Having to decide on costs versus functionality will determine how to license your server. This would be either per-server, per virtual machine needed, or per processor core and then you need CALs). If you don’t believe it, just have a look at this licensing guide!
An example
To illustrate the difference, let’s say you have an outlay of a hundred thousand dollars to acquire the software licenses for three years. This compared to a cloud-hosted package that performs the same function over the same timeframe.
You can then piggy-back off companies like Amazon and Microsoft’s security services, which then costs eight thousand dollars monthly ($96k annually).
So, within three years of using the cloud, you would have reached the $100K cap that would be spent only for licenses. You would have also saved with an extra $188K in additional services.
This is a portion of what you would have been spent on maintenance, technical support, security, upgrades, and updates.
These figures are rudimentary, but the long-term savings are noticeable as cloud service providers tend to provide value-add solutions when pricing their bundles.
Microsoft recently launched its Microsoft 365 package which includes an upgrade to the latest operating system (Windows 10 Professional or Enterprise). This is something you would have had to source and pay for separately.
Stress relievers
Software deployment and the administration of user accounts is cloud-based. This means you can do this conveniently and remotely from your PC, laptop, tablet, or even your smartphone!
This means as an IT professional, you will now have more time to oversee more important issues like data security and overall IT policies. Better yet, you would have the time to investigate ways to automate and improve your systems.
This is possible without the inconvenience of running from PC-to-PC to install operating systems, Office software, or manage mailboxes.
Remote desktop services of an on-premise server were a step in this direction – but are a pain to set up. So, you can view the cloud as an evolution of remote-desktop services.
Infrastructural setbacks
The only (and potential) hindrance to using cloud services naturally would be the availability of good and cheap broadband (Internet connectivity).
Without both, the justification for running your business fully on the cloud would not stick. Some businesses, especially in developing countries, go endure desperates attempts to adopt the cloud.
They use what is known as hybrid-systems: a combination of cloud and on-premise solutions.
If you operate in a country without forward-thinking government officials that facilitate broadband availability, you will suffer the most.
Like an old, car, outdated hardware and software can lead to costly services (out-of-date and warranty solutions). This leads to you having heftier maintenance fees and support costs by third-party IT professionals.
The old rhetoric of ‘not trusting the cloud’ is now one of the past. Cloud services often outperform on-premise solutions when it comes to high-end security software and data protection. This is because of the obvious economies of scale involved in setting up expensive security software.
The level of security has to be the digital equivalent of Fort Knox. This especially if you are dealing with sensitive data such as financial, legal services, healthcare, and educational institutions.
Your company would need a system that will keep all such data secure and data compliant.
Data is now treated as a commodity. There is now a subsequent need to trade and value it. We now have Blockchain-based solutions like IOTA to facilitate your payments. This while keeping data encrypted, decentralized, and safe.
In the advent of the new GDPR laws, some companies will still opt to keep and maintain their servers internally. By doing this, however, you might lack the transparency and tools needed to show your consumers how you handle their sensitve data.