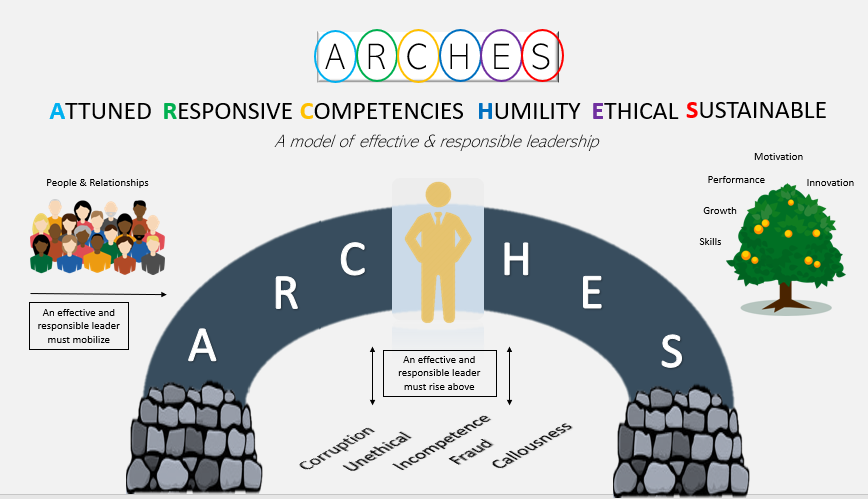
Why do people hack systems? Hacking is a technique used to compromise any digital device. Hackers want to get into your device to use your data for varied reasons – naturally, most of these motives are financially driven.
A data breach is usually what leads to a hack. There is a difference even though both terms are used interchangeably.
A data breach happens when data that is left vulnerable in an unsecured environment gets viewed by someone who shouldn’t have access to it.
While hacks are the result of malicious behavior, breaches happen as a result of negligence, human error, or other non-malicious behavior that creates a security vulnerability.
Hackers may access your device just to say they could or for financial gain, to protest, or to gather sensitive information.
So what makes a hacker?
In the past, a hacker may have been a whiz kid or specialized programmer but in the modern-day, hacking has become easier and more people are becoming hackers. As more people shop online and use computers for everyday tasks, they become the prey of hackers worldwide.
Actual hacking is technical in nature – the hacker does not communicate with the person whose PC they are hacking into.
But they can also use psychology to trick the user into clicking on a malicious attachment or providing personal data. These tactics are referred to as social engineering.
Your cellphone too can be hacked
While most associate hacking with Windows computers, the Android operating system also offers an inviting target for hackers. That means millions of people who use Samsung phones can be hacked.
Some fifty years ago, there was a name for hackers who obsessively explored low-tech methods for getting around the secure telecommunication networks and expensive long-distance calls. they were called phreaks.
This was a portmanteau of the words phone and freaks. They were a defined subculture in the 1970s, and their activity was called phreaking.
Phreakers have now evolved out of the ‘analog technology era’ to become hackers in the digital world. They are beyond a sub-culture and have become a genuine threat to the safety of our information and data.
Mobile phone hackers currently use a variety of methods to access your mobile phone and can intercept phone calls, voicemails, text messages, and even the phone’s microphone and camera, all without your permission or even knowledge.
iPhones are not safe either
In 2020, many journalists working for Al Jazeera were victims of a sophisticated zero-click spyware attack.
The Toronto-based internet watchdog group Citizen Lab was asked to look into the attacks, which took place in July and August, and they released their findings at the end of December.

The report found that 36 journalists, producers, anchors, and executives had their iPhones compromised by Pegasus spyware. The spyware, developed and sold by an Israeli-based firm called NSO Group, targets security vulnerabilities in the iMessage app.
The so-called “zero-click” exploit deploys without any user interaction. Once installed, it can record ambient sound and phone conversations, take pictures, and access user credentials. It sounds like science fiction but it’s very much real!
Types of hacks
Malware
People can use hardware to sneak malware into your PC. In offices, hackers will infiltrate networks by giving staff members infected USB sticks, dodgy USB cables, and mouse chords.
It is crucial to always think before plugging anything into your work or personal device with access to confidential data.
Educate your staff about being careful before plugging anything into their PCs.
Malware infections generally occur when users interact with dangerous code by clicking on a URL or downloading malicious software disguised as an authentic program. But zero-click spyware penetrates devices without any user interaction.
Citizen recommends making sure that your mobile OS is updated to the latest version. Identified vulnerabilities in previous versions of iOS were patched in the iOS 14 update.
Practicing good digital hygiene is always important for the security of your mobile devices.
Use sites like haveibeenpwned.com and breachalarm.com to see if your email credentials have been compromised. Use strong passwords on any apps that contain sensitive data and delete any apps that you do not regularly use.
Missing security patches
Always remember to update your security tools. Too many people ignore update notifications or security patches, leaving themselves vulnerable. It’s not just antivirus software that needs patching.
Tell your staff to ensure that all their antivirus and applications are routinely updated as security patches become available. This task is usually the job of your IT department if you have one in the first place.
Getting your password information
Hackers can obtain your credentials through several means, but commonly they do so through a practice called keystroke logging or keylogging.
Can you believe that the most common password is “123456”? Hopefully, yours isn’t so, or any of the most hacked passwords in the last 10 years.
Through a social engineering attack, you could accidentally download software that records your keystrokes, saving your usernames and passwords as you enter them.
This and other forms of spyware are malware that tracks your activity until a hacker has what they need to break into your system.
Attackers can deploy malware on a user’s machine if they are in your environment and capture your credentials via keylogging too.
Hackers also use password cracking programs that can run letter and character combinations, guessing passwords in a matter of minutes, or even seconds.
To get around this, use a password management tool that securely houses your company’s credentials. These tools can often auto-generate lengthy, diverse character passwords that are difficult for hackers to guess. They can also autofill for your employees for easy access to their tools.
Encryption and multi-factor authentication methods also offer more layers of protection.
Distributed Denial-of-Service (DDoS)

This technique involves taking down a website so that a user cannot access it or deliver their service. DoS attacks take place when hackers inundate a target’s server with large influxes of traffic. The amount is so frequent and high that it overloads the server by giving it more requests than it can handle. This crashes your server and your company’s website.
Larger businesses can get hit by a Distributed Denial of Service (DDoS) attack, which is a synchronized attack on more than one server or website, potentially taking down numerous online assets.
A good method to fight DDoS attacks is to use cloud protection services to spot them – like Acunetix or Netsparker.
Social Engineering & Phishing
This is where hackers try to get your personal information, often by impersonating a legitimate and maybe trusted source.
Many types of social engineering bait come in the form of phishing emails.
A hacker sends you a message that looks like it’s from someone you know, asking you to do something, like wire them money, or to click or download an infected attachment to see more.

“The top malicious email attachment types are .doc and .dot which make up 37%. The next highest is .exe at 19.5%,” according to a report by Symantec. Always be cautious of opening these types of attachments.
Warn your employees to never give out private business information over email, to think before opening any attachments, and educate them on mail scams.
Use email software that scans for phishing. Microsoft 365 and Google’s Business packages come equipped with such. Google’s tech uses AI to scan the content and find things such as spelling errors and dodgy URLs. This enables the system to block them before they even hit your inbox.
Most people or companies that get hacked or suffer from a data breach do so mainly due to negligence. Many do not prioritize beefing up their security systems before it is too late. Hacks are, however, completely avoidable so don’t fall victim to them.
Other ways to protect yourself
- Download a reliable anti-malware product that can both detect and neutralize malware and block connections to malicious phishing websites.
- Of course, whether you are on Windows, Android, a Mac, an iPhone, or in a business network, you must always use layered protection wherever you can.
- Only download phone apps from the legitimate marketplaces that police themselves for malware-carrying apps, such as Google Play and the Apple/Amazon Appstore.
- Check the ratings and reviews first. If it has a low rating and barely any downloads, it might be best to avoid that app.
- Use long and complex passwords. Don’t use numbers in sequence. You can also use mixes of letters that can be remembered through rhymes.
- Consider using a password manager.