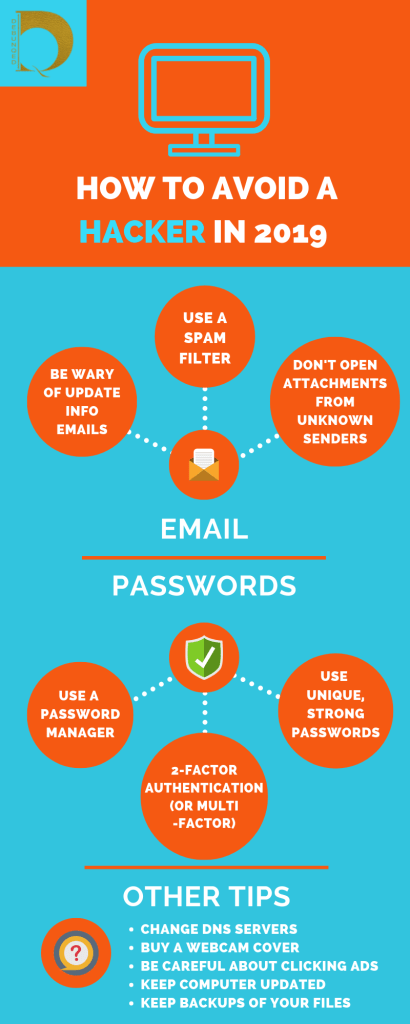
Global security breaches are on the rise and no one or country is safe. The acceleration of certain technologies has been rapid since the pandemic engulfed the world last year. But unfortunately, we’ve also become slack in the process.
Once again, it has become apparent just how ‘at-risk’ our data is.
Data hacks have been frantic and are now getting major press attention. It’s hard to know who each unwanted visitor is in each case but fingers are being pointed in perhaps familiar directions.
Russian invaders back at it again
In fact, throughout June, Russians have been blamed for a slew of hacks around the world.
Microsoft in late May said a wave of Russian cyber-attacks had targeted government agencies and human rights groups in 24 countries, mostly in the US.
It claimed that around 3000 email accounts of more than 150 different organizations, some of them international, were attacked in just one week.
Allegedly, the group responsible was the same one that carried out 2020’s SolarWinds attacks, which the Russian Foreign Intelligence Service (SVR) was accused of orchestrating.
But the Kremlin denied having any knowledge or anything to do with any cyber-attacks. It challenged Microsoft to how these attacks were linked to the European attacks.
Nevertheless, authorities are now aggressively investigating cybercrime. In the first week of June, the US Justice Department recovered around $2.3m in cryptocurrency ransom money.

This was part of the funds paid by the Colonial Pipeline Company to Russian hackers in the most disruptive cyberattack on record in the country.
The US deputy attorney general Lisa Monaco said investigators had seized 63.7 Bitcoins which was paid by the company after its systems were hacked, leading to massive shortages of petrol along the US’s East Coast. The department said it founded and recaptured the majority of the ransom.
The hackers are believed to be a group called DarkSide, whose menace caused a multi-day shutdown in certain petrol stations and a spike in gas prices.
The attack made international news and prompted the US’s White House to encourage business executives to improve security measures to avoid future cyberattacks whatever their nature, ransomware or otherwise.
The FBI said DarkSide had also disrupted operations at a meatpacking company. As no one tends to be spared in the spillover effects, it is always a good idea to protect your company’s digital assets as a preventative measure.
Not so sophisticated
The attackers rather proved to be quite ‘amatuerish’ because they sent the Bitcoins to an online platform to convert it to fiat money – and that is how they got nabbed. Server-hosted (Online) crypto exchanges are obliged to keep customer data for compliance and anti-money laundering practices. So while your Crypto digital wallet does not reveal your identity, pairing it with an exchange will link it to all the other particulars you needed to provide to use the exchange.
As long as you need cash to pay for things you will always need to switch your crypto in some way or another – unless your recipient agreed to take payment in Crypto as well. Keeping your digital assets on a hard-wallet or on your hard-drive keeps them “off-the-grid”. But also means you can’t actually spend them.
Although the initial cyberattack was a smart manuever, the attackers proved to be rookies at the robbing game in the end.
On a positive note: the ability to retrieve Bitcoins actually reinforces the need for a Blockchain-based financial system. This made it easier for the authorities to track movements of the ‘ransom-paid’ Bitcoins.
Cuban for a bruising
But politicians aren’t the only people who are urging businesses, civil society organizations, and other groups to improve security systems and be cognisant of an often-dark future.

US Dollar billionaire Mark Cuban has also called for stricter cryptocurrency regulations.
The owner of the Dallas Mavericks who has been investing in trading Bitcoin and other cryptocurrencies such as Ethereum said the world was in dire need of regulation for the burgeoning decentralized finance (DeFi) space.
Cuban said in an interview with Bloomberg that there “should be regulation to define what a Stablecoin is” in order for DeFi to be reliable and to prevent total collapses in investments.
This comes after he saw his investments in a particular Stablecoin ‘went to zero’. Cuban claimed he had been scammed.
Stablecoins are a type of cryptocurrency that is pegged to an underlying asset, or currency – usually the US dollar. They are the earliest forms of DeFi and the largest Stablecoin, Tether, is currently worth more than $62bn.
DeFi has helped the price of Ethereum, the blockchain on which most DeFi projects are built, to also soar. But they can be highly risky investments.
Investors try to create arbitrage opportunities and liquidity between coins but such a scheme collapsed for Cuban.
“There should be regulation to define what a stable coin is and what collateralization is acceptable,” he said.

Strong words of caution
Cuban hasn’t revealed how much money he lost but told a fellow DeFi investor via Twitter that regulation must be implemented- and quickly.
It had been suggested that Cuban was “rugged” which refers to when a project’s liquidity dries up and investors cannot withdraw their cash.
Mark Cuban is alleged to have 60% of his crypto holdings in Bitcoin, 30% in Ethereum, and 10% held in other coins. He likes to experiment with new financial tech investments.
He added further in a recent blog post that banks should be scared of unregulated DeFi technology.
All crypto-based investments remain highly risky as the technology around them develops. But there certainly needs to be global laws to prevent people from losing hefty amounts of their wealth/investment. Cryptocurrency is without a doubt a very lucrative investment vehicle that could make you an overnight millionaire. But that also makes it a perfect vehicle for scammers to clone projects to make away with your hard-earned cash.
You must, therefore, be extra vigilant and scrutinize offers for instant riches. But more so, you would be quite negligent these days to navigate the Internet without any form of cyber-protection.