Maybe you should encourage your kids to become hackers. When you open Twitter handles and Linkedin profiles, it’s not unlikely that you’ll find people listing hacking as a skill.
Parents used to tell their kids to become doctors, lawyers, and accountants. Later, they advised them to learn about computers. These kids have now grown to become hardware specialists and then software specialists today.
In the past 10 to twelve years, we have seen ourselves thrown into the fourth industrial revolution. In it, technology affects our lives through social media and augmented reality.
We share a lot of our personal information with more people, companies, and institutions every day, willingly and are often blasé about it. This has tempted people to steal this information by hacking it.
Hacking background
Since the advent of personal computers in the 1980s hackers have become prolific, initially in ‘first-world’ countries that had an advanced infrastructure. There were numerous cases in the US but as computer technology permeated the world, hackers followed suit.
A hacking group called MOD, Masters of Deception, in the 1980s allegedly stole passwords and technical data from Nynex, and other telephone companies as well as several big credit agencies and two major universities.
The damage caused was extensive and one company, Southwestern Bell said it suffered losses of $370,000 alone. These days the damages, though not always publically announced, can run into a few millions of dollars.
READ MORE about the Online Threats hackers use here
All this has paved the way for a special information technology (IT) vocation. A security hacker is someone who explores methods for breaching defenses and exploiting weaknesses in a computer system and networks. They break into systems they aren’t authorized to, and tend to break seamlessly into email and banking systems.

Hacking as a career
Ben Wilson works as an ethical hacker. He has more than ten years of experience and worked in London where he received on-the-job training. He now works remotely in South Africa servicing UK clients.
“I test websites for clients and look for vulnerabilities in the systems. I have done a lot of work for banks lately but my work is across industries.”
“Energy companies are using my services more and more,” he says.
Wilson says he worked in a permanent position for six years. Right now he contracts for five clients regularly.
Ethical hackers are the knights who test how permeable these systems are.
“The majority of my work is for British clients. The UK pound is strong and I like to earn pounds. I’d say the best computer security consultants in the world are in the UK. The US is strong too but the UK consultants are sophisticated and the best.”
Vulnerabilities
The most common way in which people hack information is through email contacts; especially personal Gmail accounts.
People think that their information is safe because it sits with one of the largest companies in the world. But this is exactly why it isn’t safe.
Gmail and other third-party free email accounts are regularly hacked. If you want to protect especially valuable information you should either upgrade it to the business/enterprise level, use a different email service, or perhaps the one connected to your employer.
Nowadays companies use services to protect themselves against hacks and unauthorized access. These monthly or annual service providers might employ ethical hackers to check the companies’ systems.
Hacking, however, isn’t just something that happens to big companies or in blockbuster movies. Here are some reality checks:
- All websites are under threat;
- So are applications (Apps) on your phone;
- People can also program artificial intelligence (AI) to hack into systems. This has become a big concern and theme for security experts.
Ways to proactively prevent a hack
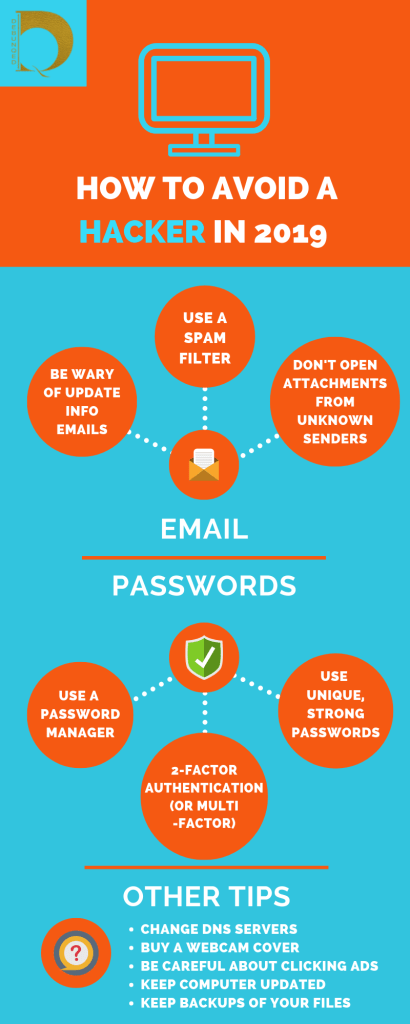
Fortunately, there are several ways of protecting yourself and your information from hacking; starting with your emails. Be wary of “phishing” emails asking you to update your information, especially for bogus databases that you have never heard of.
Use a spam filter – Avoid opening attachments from senders you don’t know – Update your passwords regularly – It helps to have authentication methods, such as a smartphone-linked and email-linked authentication (2FA) or security keys like Yubico – Do not click on any ad – period! Back up your files regularly – it’s always a good idea – Don’t allow ransomware bullies to bully you.
- If you get sent communication saying that people have your files and want money or they’ll release the files; ignore them.
- They can’t threaten you forever and might eventually move onto another target especially if your information loses its value over time.
Anti-hacking software

As a business, use tools like those from cybersecurity experts Acunetix. More than 4 000 companies protect their web applications from vulnerabilities using its powerful web scanner.
Its penetration testing software prevents potential attacks by identifying holes in your websites’ coding. This is where hackers usually plant their complex code which allows them to extract data such as contact details, credit card details, and in worse cases, company-sensitive data like patents and blueprints.
Naturally, it also scans networks to find gateway loopholes that could lead to crashes and downtime-related losses. A bank’s website going down for a few hours can cost it several thousand or even millions in lost revenue.
Despite having firewalls, VPNs, and other Internet security systems in place, your websites and apps being developed are still vulnerable to cyber-attacks or a hack.
The most commonly known hack used is a DDoS attack. Basically, it works like a traffic jam clogging up a highway, preventing regular traffic from arriving at its desired destination. Incidentally, only a few days ago, Amazon was hit by a DDoS Attack.
So, how would you know or find out if you are vulnerable? By conducting regular scans on your websites and apps to see where vulnerabilities lie.
Avoiding a hack requires common sense
Be aware and don’t fall into scams. It’s unlikely you’ve won 120-million Euros in a lottery. You should know by now that you are not the descendant of a king!
In addition, if someone says they have a sex tape with you in it and they want your salary, unless you know you made a sex tape, they’re probably lying.
Unless of course, a scorned lover of yours tricked you – but you can’t blame technology or a hacker for that.